How it Works
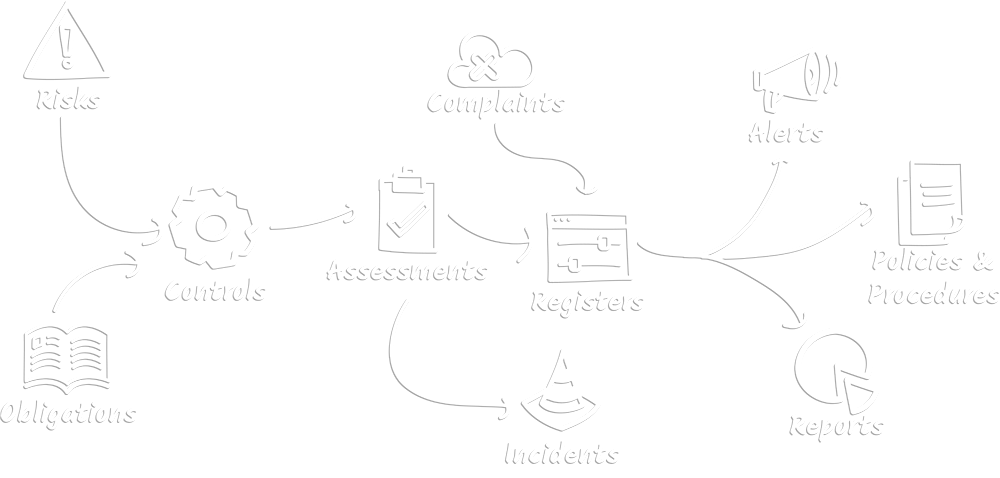
CRS Certus becomes your record of your risks, risk profile, risk mitigators, obligations, responsible managers and staff, policies and procedures. It holds your proof of control execution. It facilitates recording and managing issues, incidents and complaints. CRS Certus can be interrogated to deliver reports on all data it holds in a format your audience needs.
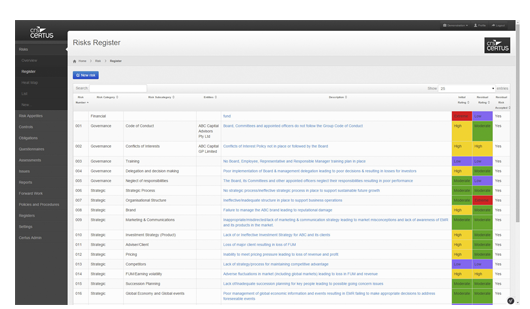
Risks
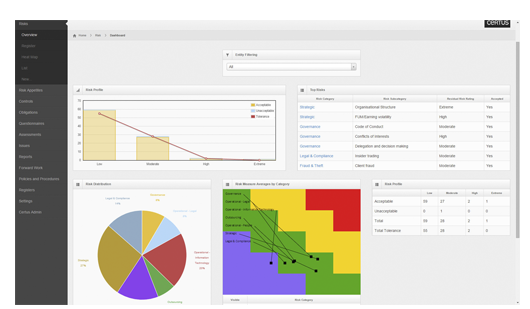
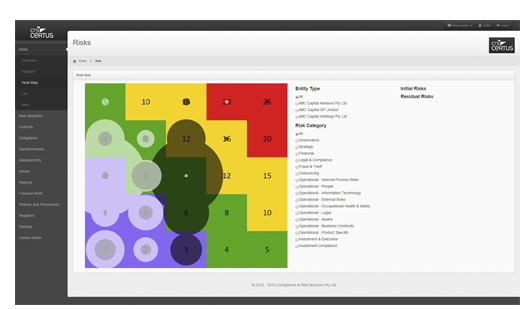
Full risk management system. Customisable risk register. Multiple entity ratings support. Links to mitigating controls and issues register. Risk appetites tied to strategic objectives. Risk tolerance triggers and questionnaire system.
Obligations
Record obligations. Link to legislative or regulatory sources. Reconcile obligations with business controls
Controls
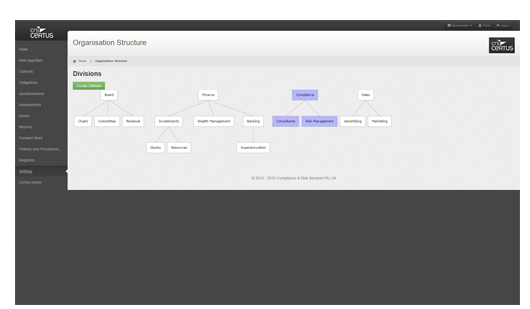
Document business controls. Link to risks and obligations. Assign responsibilities to managers. Automatically generate controls self-assessment questionnaires. Managers alerted when questionnaires are ready, complete within CRS Certus
Assessments
Controls response assessment navigation. Record testing results. Full audit records of resolution and further action. Directly load adverse responses into Issues Register.
Incidents
Capture incidents originating from within CRS Certus and reported by your business. Customise incident categories. Workflow management. Assign activities. Capture reportability assessment, related documents and developments.
Complaints
Customise complaint categories. Seamless flag as incidents, breaches or risk mitigation controls failures.
Registers
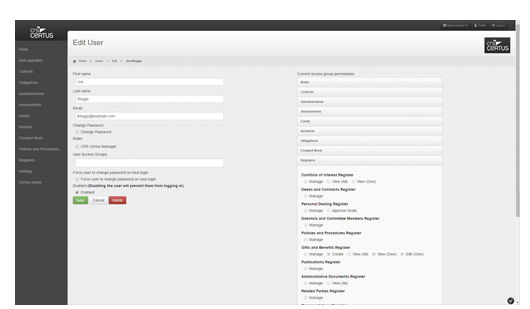
Breach register with regulator reporting assessments. Personal dealing approvals and register, gifts & benefits, training, conflicts of interest, relatedy party, legal documents, administrative documents, publications, office holder registers amongst others.
Alerts
Email alerts issued out of the system directed to your defined positions. Customisable email content and triggers. Email service log validates that communications are sent.
Policies & Procedures
Policies and procedures library. Alert users to new content to review within CRS Certus. Capture user confirms of access and understanding of policies and procedures. The library becomes your single point of truth.
Reporting
Flexible reporting to PDF and XLS(X). Customisable report content, period and presentation, tailored and relevant for the audience. Reports returned immediately. Aides regulatory enquiry, annual audit, demonstrates the control you have over your business